KRACK; all you need to know about the Wi-Fi vulnerability
 This week, researchers published information on a serious weakness in WPA2, the security protocol that protects most modern Wi-Fi networks.
This week, researchers published information on a serious weakness in WPA2, the security protocol that protects most modern Wi-Fi networks.
The flaw in WPA2 allows anyone to break the security layer that is established between a wireless device and the targeted Wi-Fi network, essentially exposing network traffic, including passwords, chat messages and photos to the attackers.
KRACK
The practise of exploiting this vulnerability has eloquently been named KRACK, an acronym for Key Reinstallation AttaCK.
The reasoning behind the name comes from the fact that this type of attack tricks a victim into installing an already in-use key to their device (a piece of code that allows an attacker to decrypt encrypted network traffic).
In theory, every key on every device should be unique, but this vulnerability in WPA2 allows hackers to manipulate communications between routers and devices so that the keys can be reused. This can lead to the decryption of traffic on an affected network.
The recently discovered WPA2 weakness is present in the Wi-Fi standard itself; it is not a vulnerability in an individual product or a specific implementation. This means that every instance of WPA2 contains the weakness, thus impacting a wide range of devices and operating systems, from Android and Apple to Linux and Windows.
As a result, any attack that attempts to exploit the WPA2 weakness must do so within range of the wireless signal between the device and the Wi-Fi network. From a defensive perspective, this is a good thing, as it prevents the attack from being launched remotely.
Furthermore, industry best practices call for sensitive data being transferred on the network to be protected using Secure Sockets Layer (SSL) encryption, which sits above the network-layer WPA2 protections.
In summary, for the WPA2 weakness to be exploited, the attacker must be physically co-located near the wireless signal he is trying to compromise. Even if the attacker is successful in compromising the Wi-Fi signal via the WPA2 weakness, sensitive data being sent over that channel would likely be encrypted using SSL, ensuring it is still protected from the attacker.
KRACK: the details
The recently discovered WPA2 weakness is present in the Wi-Fi standard itself; it is not a vulnerability in an individual product or a specific implementation. This means that every instance of WPA2 contains the weakness, thus impacting a wide range of devices and operating systems, from Android and Apple to Linux and Windows.
As a result, any attack that attempts to exploit the WPA2 weakness must do so within range of the wireless signal between the device and the Wi-Fi network. From a defensive perspective, this is a good thing, as it prevents the attack from being launched remotely.
Furthermore, industry best practices call for sensitive data being transferred on the network to be protected using Secure Sockets Layer (SSL) encryption, which sits above the network-layer WPA2 protections.
In summary, for the WPA2 weakness to be exploited, the attacker must be physically co-located near the wireless signal he is trying to compromise. Even if the attacker is successful in compromising the Wi-Fi signal via the WPA2 weakness, sensitive data being sent over that channel would likely be encrypted using SSL, ensuring it is still protected from the attacker.
Wandera’s protection
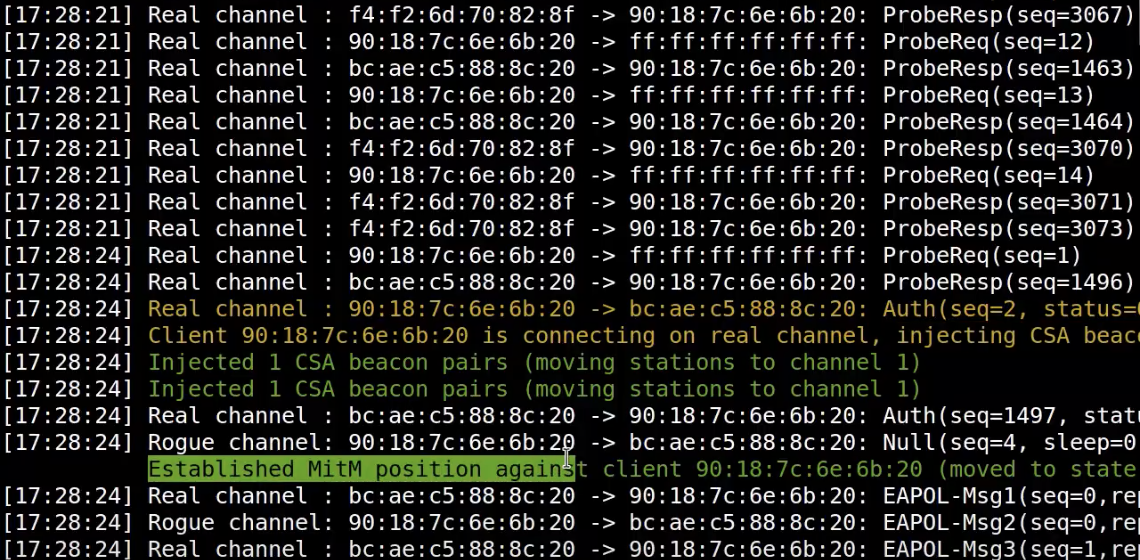
 Wandera has multiple mechanisms in-place to monitor for network-based threats. These include man-in-the-middle (MitM) attacks, rogue hotspots and protocols attacks such as SSL Strip. In addition, Wandera monitors apps and sites in real-time for sensitive data leaks and can raise alerts and enforce policy blocks when these leaks occur.
Wandera has multiple mechanisms in-place to monitor for network-based threats. These include man-in-the-middle (MitM) attacks, rogue hotspots and protocols attacks such as SSL Strip. In addition, Wandera monitors apps and sites in real-time for sensitive data leaks and can raise alerts and enforce policy blocks when these leaks occur.
This means that Wandera is able to ensure that the SSL encryption is protected, even if a successful KRACK attack is launched.
Wandera is continuously monitoring the vulnerabilities associated with this type of attack. Once mobile vendors confirm the affected OS versions we will automatically incorporate this information into our outdated OS assessment in order to notify users and admins to upgrade their software.